Introducing selective Lambdafication
“Lambdafication” is the automated transformation of source code to make it run on AWS Lambda. It is a provider-specific flavour of generic “FaaSification” which is our ultimate research goal. With our Lambdafication tooling, we offer application engineers today the possibility to step into the serverless world without much effort, and leave the more challenging research tasks for the summer time.
Continuing the Java Lambdafication topic, started with the Java translation tool for AWS Lambda called Podilizer, we inform about the open source launch of Termite, a buildtime/runtime library for Lambdafication. And here is logical question: “Why do we need another tool which essentially does the same job as Podilizer?” The reasons come from experience we gained prototyping, developing and field-testing Podilizer. One of them is the quality of translation of some complex projects (Java OOP/functional programming paradigm issues). Another one touches the code design: FaaS does not position itself as a new full cloud deployment method, furthermore native design of serverless fits the idea of going along with other projects and infrastructures. We assume that functions could take care about particular tasks in the cloud or become a glue between existing microservices. Based on this knowledge we created Termite, which tends to fit current FaaS paradigms by letting application engineers choose which methods to export.
Termite vs Podilizer
Unlike Podilizer, which is implemented as command-line tool and unconditionally translates a whole project’s source code, Termite’s design allows to translate certain methods into Lambda functions. It provides syntax elements to mark methods in your project and have them translated and uploaded as lambda functions in a controlled way. Not a less important advantage of Termite is auto-generating dependencies for each function, leading to easier configuration. On the other hand, Podilizer is able to handle between-functions calls, while Termite does not give you such opportunity (yet). Overall Termite looks more harmonious and flexible compare to Podilizer despite the limited maturity.
Architecture and design
The core idea of the design are Java annotations as a syntactical means to mark and configure functions. As long as annotations are part of the language they are easy in understanding and usage. An example for marking a method with annotations follows:
@Lambda() public static int sum(int a1, int a2){ return a1 + a2; }
The syntax makes it possible to configure Lambda function aspects such as resource use and placement:
@Lambda(timeOut = 60, memorySize = 512, region="us-west-2") public static int sum(int a1, int a2){ return a1 + a2; }
Annotated methods are being processed over the compilation phase. The Termite processor creates Lambda functions based on the particular method specification and uploads them to the cloud. Function invocation is performed through the AspectJ library. AspectJ interrupts the runtime workflow and calls deployed Lambda functions instead of local methods, as shown in the following high-level diagram.
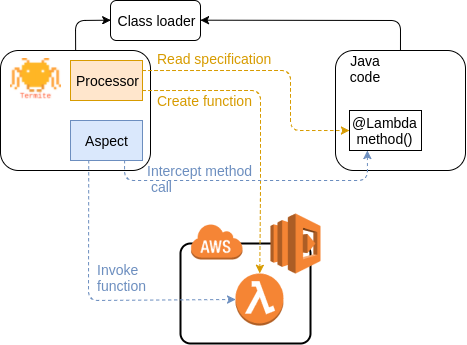
How to use
Before using Termite directly from our Git repository, make sure to fulfil the following prerequisites:
- AWS account and credentials configured at your machine (aws command-line tool should work: aws lambda list-functions)
- JDK 1.8+ installed
- Maven installed
Clone from https://github.com/serviceprototypinglab/termite (In the folder ‘example’ you can find example project which uses Termite):
clone https://github.com/serviceprototypinglab/termite.git
Compile the project:
cd termite mvn clean install
Afterwards, Termite is ready to be used within your Java application. Assuming you use Maven, create your own Maven project and configure dependencies. In case you use another build system, Termite does not offer integration yet but we are happy to accept patches of course.
<dependency> <groupId>ch.zhaw.splab.servicetooling</groupId> <artifactId>Termite</artifactId> <version>0.1</version> </dependency> <dependency> <groupId>org.aspectj</groupId> <artifactId>aspectjweaver</artifactId> <version>${aspectj.version}</version> <scope>runtime</scope> </dependency>
Correct execution is able only with the following argument to the Maven execution plugin:
-javaagent:${settings.localRepository}/org/aspectj/aspectjweaver/${aspectj.version}/ aspectjweaver-${aspectj.version}.jar
Also you need the generic Maven plugin for compiling generated sources because Termite will generate some source code files:
<plugin> <groupId>org.bsc.maven</groupId> <artifactId>maven-processor-plugin</artifactId> <version>2.2.4</version> <executions> <execution> <id>process</id> <goals> <goal>process</goal> </goals> <phase>process-sources</phase> <configuration> <proc>none</proc> <outputDirectory>${generated.sources.directory}</outputDirectory> <processors> <processor>ch.zhaw.splab.podilizerproc.annotations.LambdaProcessor </processor> </processors> </configuration> </execution> </executions> </plugin>
A full example of a Maven configuration file is located in the Termite repository at
example/pom.xml
Afterwards, you’re ready to go serverless! Annotate functions you want to upload with “@Lambda”, see the example above.
Compile the created project:
mvn clean install
Maven will inform you about deployed functions which are then ready to be used from AWS Lambda. We’d like to hear from your experience with using Termite – do not hesitate to comment on this post.
Thanx for the great article…
Its very basic.. its help me a lot..
but i want to ask you about Polymorphism..
did you have an article about it??
Thanx…
Is this concept is new in java or what. Because i heard frist time about this.
Graet that i find this article.
Write is easyily understandable.
Thanks for the sharing
With our Lambdafication tooling, It offer application engineers today the possibility to step into the serverless world without much effort.
Java methods are often stateful through instance attributes. The state handling of the resulting decomposed functions can either extend the method signature to pass in and out all attributes which are accessed and modified, or use server-side state. AWS Lambda offers both an S3 blob storage interface and local environment variables. However, the variables are restricted to read-only access from the runtime
Wonderful article for the deatil understanding.
Looking forward to see the next post.
Looking great work! I really appreciated to you on this quality work. The article contains detailed information about selective Lambdafication and for me it’s really easy to understand. Thanks for sharing this concept. keep up the great work!
Yes absolutely truly said..!!Keep up the work.
Agreed!
I’m working on the multiplatformization of Termite for months now and I was struggling a lot of times. … And it is not only slow because of Java, slowness is amplified by the gradle-scripts that … iOS and it’s API’s became way too complicated.
This is likewise a decent post which I truly appreciated perusing. It isn’t each day that I have the likelihood to see something like this..
Wonderful article
Great post about. I am doing internship it is very helpful for me.
Thank you for providing this information, I am currently working on Research and I found this post and it’s most useful. This would be the best place to source all the necessary information for beginners.
Thank you so much for sharing all this wonderful information !!!! It is so appreciated!! You have good humor in your blogs. So much helpful and easy to read!
Wonderful Article.
looking forward to what’s in store next